Usually, you have already other services running in your raspberry and so, TCP port 80 and 443 (HTTP and HTTPS) are already being used.
In this case, you will need to configure a reverse proxy to handle the requests received in your Raspberry to the right docker. In this post, I will share the steps I followed for this (provided you already had an nginx running in your Raspberry).
- Create a new site config for nginx:
sudo vi /etc/nginx/sites-available/fmsdevel.wisecoding.es.config
And write the following (please note you need to change "fmsdevel.wisecoding.es" to your specific configuration:
server {
listen 80;
listen [::]:80;
server_name fmsdevel.wisecoding.es;
location / {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
proxy_set_header X-NginX-Proxy true;
proxy_pass http://127.0.0.1:2368;
}
}
- Enable the new configuration and reload nginx
sudo ln -s /etc/nginx/sites-available/fmsdevel.wisecoding.es.config /etc/nginx/sites-enabled/fmsdevel.wisecoding.es.config
systemctl reload nginx
-
Now, our Ghost servers is ready to receive requests from the Internet. Change the DNS to map your name (in the example above, fmsdevel.wisecoding.es, to your public IP where your NGINX is already working)
-
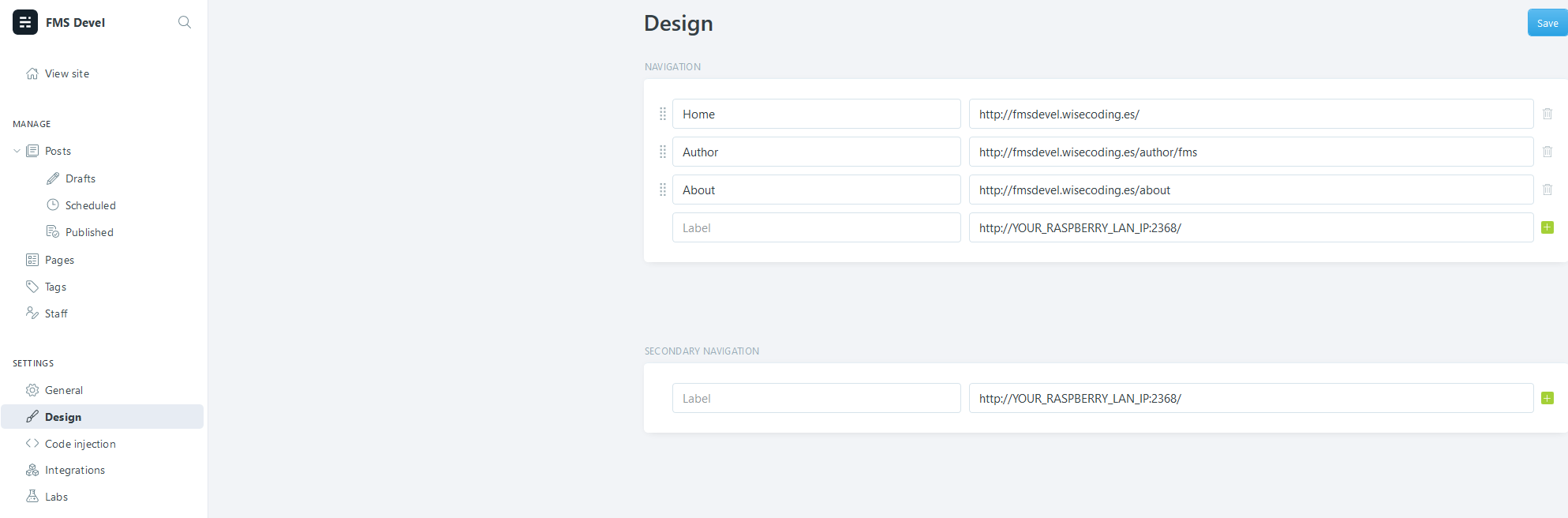
As now your blog is in the Internet, I suggest configuring the new DNS name in the Ghost configuration under:
http://<YOUR_RASPBERRY_LAN_IP>:2368/ghost/#/settings/design
So it changes to something like this:
- If we're using cert bot for getting Let's Encrypt certificates, now we're ready to also protect our blog with SSL
sudo certbot --nginx -d fmsdevel.wisecoding.es
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator nginx, Installer nginx
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for fmsdevel.wisecoding.es
Waiting for verification...
Cleaning up challenges
Deploying Certificate to VirtualHost /etc/nginx/sites-enabled/fmsdevel.wisecoding.es.config
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Redirecting all traffic on port 80 to ssl in /etc/nginx/sites-enabled/fmsdevel.wisecoding.es.config
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations! You have successfully enabled https://fmsdevel.wisecoding.es
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=fmsdevel.wisecoding.es
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/fmsdevel.wisecoding.es/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/fmsdevel.wisecoding.es/privkey.pem
Your cert will expire on 2021-04-07. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the "certonly" option. To non-interactively renew *all* of
your certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Remember to change the Ghost settings URLs to use https